| Chapter 3. Installing Guacamole with Docker | ||
|---|---|---|
| Prev | Part I. User's Guide | Next |
- Docker Postgres Install Extension Tool
- Docker Postgres Install Extension Chrome
- Docker Postgres Install Extension Tutorial
- Docker Compose Postgres Install Extension
- Docker Postgres Install Extensions
Installing Extensions¶ Our official Docker image comes with Power Pack and Review Bot pre-installed. If you need to install additional extensions, you’ll need to build an image. Create a directory where your Dockerfile will live. If you’re installing custom extensions, create a packages/ directory inside it and place your extension.whl.
- Docker provides a way out of this mess by reducing the task of installing and running software to as little as two commands (docker run and docker pull). In this post we will see this process in action by taking a step by step look at how easy and simple it is to setup a Postgres installation with docker.
- To deploy a Postgres container using Docker Compose, you should have this Docker tool set up on your system. If you are a Linux user and need help setting up, refer to one of our guides on installing Docker Compose on Ubuntu or how to install Docker Compose on CentOS.
Table of Contents
- Running the guacd Docker image
- Running guacd for use by the Guacamole Docker image
- Running guacd for use by services outside Docker
- The Guacamole Docker image
- Configuring Guacamole when using Docker
- Connecting Guacamole to guacd
- MySQL authentication
- PostgreSQL authentication
- LDAP authentication
- Header Authentication
- Custom extensions and
GUACAMOLE_HOME - Verifying the Guacamole install
Guacamole can be deployed using Docker, removing the need to build guacamole-server from source or configure the web application manually. The Guacamole project provides officially-supported Docker images for both Guacamole and guacd which are kept up-to-date with each release.
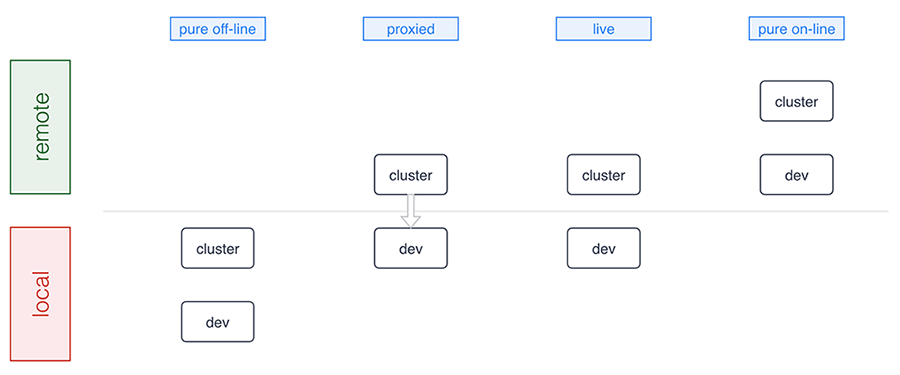
A typical Docker deployment of Guacamole will involve three separate containers, linked together at creation time:
guacamole/guacdProvides the guacd daemon, built from the released guacamole-server source with support for VNC, RDP, SSH, telnet, and Kubernetes.
guacamole/guacamoleProvides the Guacamole web application running within Tomcat 8 with support for WebSocket. The configuration necessary to connect to guacd, MySQL, PostgreSQL, LDAP, etc. will be generated automatically when the image starts based on Docker links or environment variables.
mysql or postgresqlProvides the database that Guacamole will use for authentication and storage of connection configuration data.
This separation is important, as it facilitates upgrades and maintains proper separation of concerns. With the database separate from Guacamole and guacd, those containers can be freely destroyed and recreated at will. The only container which must persist data through upgrades is the database.
The guacd Docker image is built from the released guacamole-server source with support for VNC, RDP, SSH, telnet, and Kubernetes. Common pitfalls like installing the required dependencies, installing fonts for SSH, telnet, or Kubernetes, and ensuring the FreeRDP plugins are installed to the correct location are all taken care of. It will simply just work.
Running guacd for use by the Guacamole Docker image
When running the guacd image with the intent of linking to a Guacamole container, no ports need be exposed on the network. Access to these ports will be handled automatically by Docker during linking, and the Guacamole image will properly detect and configure the connection to guacd.
When run in this manner, guacd will be listening on its default port 4822, but this port will only be available to Docker containers that have been explicitly linked to some-guacd
The log level of guacd can be controlled with the GUACD_LOG_LEVEL environment variable. The default value is info
If you are not going to use the Guacamole image, you can still leverage the guacd image for ease of installation and maintenance. By exposing the guacd port, 4822, services external to Docker will be able to access guacd.
Important
Take great care when doing this - guacd is a passive proxy and does not perform any kind of authentication.
If you do not properly isolate guacd from untrusted parts of your network, malicious users may be able to use guacd as a jumping point to other systems.
guacd will now be listening on port 4822, and Docker will expose this port on the same server hosting Docker. Other services, such as an instance of Tomcat running outside of Docker, will be able to connect to guacd directly.
The Guacamole Docker image is built on top of a standard Tomcat 8 image and takes care of all configuration automatically. The configuration information required for guacd and the various authentication mechanisms are specified with environment variables or Docker links given when the container is created.
Important
If using PostgreSQL or MySQL for authentication, you will need to initialize the database manually. Guacamole will not automatically create its own tables, but SQL scripts are provided to do this.
Once the Guacamole image is running, Guacamole will be accessible at http://, where HOSTNAME:8080/guacamole/HOSTNAME is the hostname or address of the machine hosting Docker.
When running Guacamole using Docker, the traditional approach to configuring Guacamole by editing guacamole.properties is less convenient. When using Docker, you may wish to make use of the enable-environment-properties configuration property, which allows you to specify values for arbitrary Guacamole configuration properties using environment variables. This is covered in Chapter 5, Configuring Guacamole.
The Guacamole Docker image needs to be able to connect to guacd to establish remote desktop connections, just like any other Guacamole deployment. The connection information needed by Guacamole will be provided either via a Docker link or through environment variables.
If you will be using Docker to provide guacd, and you wish to use a Docker link to connect the Guacamole image to guacd, the connection details are implied by the Docker link:
If you are not using Docker to provide guacd, you will need to provide the network connection information yourself using additional environment variables:
| Variable | Description |
|---|---|
GUACD_HOSTNAME | The hostname of the guacd instance to use to establish remote desktop connections. This is required if you are not using Docker to provide guacd. |
GUACD_PORT | The port that Guacamole should use when connecting to guacd. This environment variable is optional. If not provided, the standard guacd port of 4822 will be used. |
The GUACD_HOSTNAME and, if necessary, GUACD_PORT environment variables can thus be used in place of a Docker link if using a Docker link is impossible or undesirable:
A connection to guacd is not the only thing required for Guacamole to work; some authentication mechanism needs to be configured, as well. MySQL, PostgreSQL, and LDAP are supported for this, and are described in more detail in the sections below. If the required configuration options for at least one authentication mechanism are not provided, the Guacamole image will not be able to start up, and you will see an error.
To use Guacamole with the MySQL authentication backend, you will need either a Docker container running the mysql image, or network access to a working installation of MySQL. The connection to MySQL can be specified using either environment variables or a Docker link.
If your database is not already initialized with the Guacamole schema, you will need to do so prior to using Guacamole. A convenience script for generating the necessary SQL to do this is included in the Guacamole image.
To generate a SQL script which can be used to initialize a fresh MySQL database as documented in Chapter 6, Database authentication:
Alternatively, you can use the SQL scripts included with the database authentication.
Once this script is generated, you must:
Create a database for Guacamole within MySQL, such as
guacamole_db.Create a user for Guacamole within MySQL with access to this database, such as
guacamole_userRun the script on the newly-created database.
The process for doing this via the mysql utility included with MySQL is documented in Chapter 6, Database authentication.
If your MySQL database is provided by another Docker container, and you wish to use a Docker link to connect the Guacamole image to your database, the connection details are implied by the Docker link itself:
If you are not using Docker to provide your MySQL database, you will need to provide the network connection information yourself using additional environment variables:
| Variable | Description |
|---|---|
MYSQL_HOSTNAME | The hostname of the database to use for Guacamole authentication. This is required if you are not using Docker to provide your MySQL database. |
MYSQL_PORT | The port that Guacamole should use when connecting to MySQL. This environment variable is optional. If not provided, the standard MySQL port of 3306 will be used. |
The MYSQL_HOSTNAME and, if necessary, MYSQL_PORT environment variables can thus be used in place of a Docker link if using a Docker link is impossible or undesirable:
Note that a Docker link to guacd (the --link some-guacd:guacd option above) is not required any more than a Docker link is required for MySQL. The connection information for guacd can be specified using environment variables, as described in the section called “Connecting Guacamole to guacd”.
Using MySQL for authentication requires additional configuration parameters specified via environment variables. These variables collectively describe how Guacamole will connect to MySQL:
| Variable | Description |
|---|---|
MYSQL_DATABASE | The name of the database to use for Guacamole authentication. |
MYSQL_USER | The user that Guacamole will use to connect to MySQL. |
MYSQL_PASSWORD | The password that Guacamole will provide when connecting to MySQL as |
If any required environment variables are omitted, you will receive an error message in the logs, and the image will stop. You will then need to recreate the container with the proper variables specified.
Additional optional environment variables may be used to override Guacamole's default behavior with respect to concurrent connection use by one or more users. Concurrent use of connections and connection groups can be limited to an overall maximum and/or a per-user maximum:
| Variable | Description |
|---|---|
MYSQL_ABSOLUTE_MAX_CONNECTIONS | The absolute maximum number of concurrent connections to allow at any time, regardless of the Guacamole connection or user involved. If set to '0', this will be unlimited. Because this limit applies across all Guacamole connections, it cannot be overridden if set. By default, the absolute total number of concurrent connections is unlimited ('0'). |
MYSQL_DEFAULT_MAX_CONNECTIONS | The maximum number of concurrent connections to allow to any one Guacamole connection. If set to '0', this will be unlimited. This can be overridden on a per-connection basis when editing a connection. By default, overall concurrent use of connections is unlimited ('0'). |
MYSQL_DEFAULT_MAX_GROUP_CONNECTIONS | The maximum number of concurrent connections to allow to any one Guacamole connection group. If set to '0', this will be unlimited. This can be overridden on a per-group basis when editing a connection group. By default, overall concurrent use of connection groups is unlimited ('0'). |
MYSQL_DEFAULT_MAX_CONNECTIONS_PER_USER | The maximum number of concurrent connections to allow a single user to maintain to any one Guacamole connection. If set to '0', this will be unlimited. This can be overridden on a per-connection basis when editing a connection. By default, per-user concurrent use of connections is unlimited ('0'). |
MYSQL_DEFAULT_MAX_GROUP_CONNECTIONS_PER_USER | The maximum number of concurrent connections to allow a single user to maintain to any one Guacamole connection group. If set to '0', this will be unlimited. This can be overridden on a per-group basis when editing a connection group. By default, per-user concurrent use of connection groups is limited to one ('1'), to prevent a balancing connection group from being completely exhausted by one user alone. |
To use Guacamole with the PostgreSQL authentication backend, you will need either a Docker container running the postgres image, or network access to a working installation of PostgreSQL. The connection to PostgreSQL can be specified using either environment variables or a Docker link.
If your database is not already initialized with the Guacamole schema, you will need to do so prior to using Guacamole. A convenience script for generating the necessary SQL to do this is included in the Guacamole image.
To generate a SQL script which can be used to initialize a fresh PostgreSQL database as documented in Chapter 6, Database authentication:
Alternatively, you can use the SQL scripts included with the database authentication.
Once this script is generated, you must:
Create a database for Guacamole within PostgreSQL, such as
guacamole_db.Run the script on the newly-created database.
Create a user for Guacamole within PostgreSQL with access to the tables and sequences of this database, such as
guacamole_user
The process for doing this via the psql and createdb utilities included with PostgreSQL is documented in Chapter 6, Database authentication.
If your PostgreSQL database is provided by another Docker container, and you wish to use a Docker link to connect the Guacamole image to your database, the connection details are implied by the Docker link itself:
If you are not using Docker to provide your PostgreSQL database, you will need to provide the network connection information yourself using additional environment variables:
| Variable | Description |
|---|---|
POSTGRES_HOSTNAME | The hostname of the database to use for Guacamole authentication. This is required if you are not using Docker to provide your PostgreSQL database. |
POSTGRES_PORT | The port that Guacamole should use when connecting to PostgreSQL. This environment variable is optional. If not provided, the standard PostgreSQL port of 5432 will be used. |
The POSTGRES_HOSTNAME and, if necessary, POSTGRES_PORT environment variables can thus be used in place of a Docker link if using a Docker link is impossible or undesirable:
Note that a Docker link to guacd (the --link some-guacd:guacd option above) is not required any more than a Docker link is required for PostgreSQL. The connection information for guacd can be specified using environment variables, as described in the section called “Connecting Guacamole to guacd”.
Using PostgreSQL for authentication requires additional configuration parameters specified via environment variables. These variables collectively describe how Guacamole will connect to PostgreSQL:
| Variable | Description |
|---|---|
POSTGRES_DATABASE | The name of the database to use for Guacamole authentication. |
POSTGRES_USER | The user that Guacamole will use to connect to PostgreSQL. |
POSTGRES_PASSWORD | The password that Guacamole will provide when connecting to PostgreSQL as |
If any required environment variables are omitted, you will receive an error message in the logs, and the image will stop. You will then need to recreate the container with the proper variables specified.
Additional optional environment variables may be used to override Guacamole's default behavior with respect to concurrent connection use by one or more users. Concurrent use of connections and connection groups can be limited to an overall maximum and/or a per-user maximum:
| Variable | Description |
|---|---|
POSTGRES_ABSOLUTE_MAX_CONNECTIONS | The absolute maximum number of concurrent connections to allow at any time, regardless of the Guacamole connection or user involved. If set to '0', this will be unlimited. Because this limit applies across all Guacamole connections, it cannot be overridden if set. By default, the absolute total number of concurrent connections is unlimited ('0'). |
POSTGRES_DEFAULT_MAX_CONNECTIONS | The maximum number of concurrent connections to allow to any one Guacamole connection. If set to '0', this will be unlimited. This can be overridden on a per-connection basis when editing a connection. By default, overall concurrent use of connections is unlimited ('0'). |
POSTGRES_DEFAULT_MAX_GROUP_CONNECTIONS | The maximum number of concurrent connections to allow to any one Guacamole connection group. If set to '0', this will be unlimited. This can be overridden on a per-group basis when editing a connection group. By default, overall concurrent use of connection groups is unlimited ('0'). |
POSTGRES_DEFAULT_MAX_CONNECTIONS_PER_USER | The maximum number of concurrent connections to allow a single user to maintain to any one Guacamole connection. If set to '0', this will be unlimited. This can be overridden on a per-connection basis when editing a connection. By default, per-user concurrent use of connections is unlimited ('0'). |
POSTGRES_DEFAULT_MAX_GROUP_CONNECTIONS_PER_USER | The maximum number of concurrent connections to allow a single user to maintain to any one Guacamole connection group. If set to '0', this will be unlimited. This can be overridden on a per-group basis when editing a connection group. By default, per-user concurrent use of connection groups is limited to one ('1'), to prevent a balancing connection group from being completely exhausted by one user alone. |
Optional environment variables may also be used to override Guacamole's default behavior with respect to timeouts at the database and network level:
| Variable | Description |
|---|---|
POSTGRES_DEFAULT_STATEMENT_TIMEOUT | The number of seconds the driver will wait for a response from the database, before aborting the query. A value of 0 (the default) means the timeout is disabled. |
POSTGRES_SOCKET_TIMEOUT | The number of seconds to wait for socket read operations. If reading from the server takes longer than this value, the connection will be closed. This can be used to handle network problems such as a dropped connection to the database. Similar to |
To use Guacamole with the LDAP authentication backend, you will need network access to an LDAP directory. Unlike MySQL and PostgreSQL, the Guacamole Docker image does not support Docker links for LDAP; the connection information must be specified using environment variables:
| Variable | Description |
|---|---|
LDAP_HOSTNAME | The hostname or IP address of your LDAP server. |
LDAP_PORT | The port your LDAP server listens on. By default, this will be 389 for unencrypted LDAP or LDAP using STARTTLS, and 636 for LDAP over SSL (LDAPS). |
LDAP_ENCRYPTION_METHOD | The encryption mechanism that Guacamole should use when communicating with your LDAP server. Legal values are 'none' for unencrypted LDAP, 'ssl' for LDAP over SSL/TLS (commonly known as LDAPS), or 'starttls' for STARTTLS. If omitted, encryption will not be used. |
Only the LDAP_HOSTNAME variable is required, but you may also need to specify LDAP_PORT or LDAP_ENCRYPTION_METHOD if your LDAP directory uses encryption or listens on a non-standard port:
Note that a Docker link to guacd (the --link some-guacd:guacd option above) is not required. Similar to LDAP, the connection information for guacd can be specified using environment variables, as described in the section called “Connecting Guacamole to guacd”.
Using LDAP for authentication requires additional configuration parameters specified via environment variables. These variables collectively describe how Guacamole will query your LDAP directory:

| Variable | Description |
|---|---|
LDAP_USER_BASE_DN | The base of the DN for all Guacamole users. All Guacamole users that will be authenticating against LDAP must be descendents of this base DN. |
As with the other authentication mechanisms, if any required environment variables are omitted (including those required for connecting to the LDAP directory over the network), you will receive an error message in the logs, and the image will stop. You will then need to recreate the container with the proper variables specified.
Additional optional environment variables may be used to configure the details of your LDAP directory hierarchy, or to enable more flexible searching for user accounts:
| Variable | Description |
|---|---|
LDAP_GROUP_BASE_DN | The base of the DN for all groups that may be referenced within Guacamole configurations using the standard seeAlso attribute. All groups which will be used to control access to Guacamole configurations must be descendents of this base DN. If this variable is omitted, the seeAlso attribute will have no effect on Guacamole configurations. |
LDAP_SEARCH_BIND_DN | The DN (Distinguished Name) of the user to bind as when authenticating users that are attempting to log in. If specified, Guacamole will query the LDAP directory to determine the DN of each user that logs in. If omitted, each user's DN will be derived directly using the base DN specified with |
LDAP_SEARCH_BIND_PASSWORD | The password to provide to the LDAP server when binding as |
LDAP_USERNAME_ATTRIBUTE | The attribute or attributes which contain the username within all Guacamole user objects in the LDAP directory. Usually, and by default, this will simply be 'uid'. If your LDAP directory contains users whose usernames are dictated by different attributes, multiple attributes can be specified here, separated by commas, but beware: doing so requires that a search DN be provided with |
LDAP_CONFIG_BASE_DN | The base of the DN for all Guacamole configurations. If omitted, the configurations of Guacamole connections will simply not be queried from the LDAP directory, and you will need to store them elsewhere, such as within a MySQL or PostgreSQL database. |
As documented in Chapter 7, LDAP authentication, Guacamole does support combining LDAP with a MySQL or PostgreSQL database, and this can be configured with the Guacamole Docker image, as well. Each of these authentication mechanisms is independently configurable using their respective environment variables, and by providing the required environment variables for multiple systems, Guacamole will automatically be configured to use each when the Docker image starts.

The header authentication extension can be used to authenticate Guacamole through a trusted third-party server, where the authenticated user's username is passed back to Guacamole via a specific HTTP header. The following are valid Docker variables for enabling and configuring header authentication:
| Variable | Description |
|---|---|
HEADER_ENABLED | Enables authentication via the header extension, which causes the extension to be loaded when Guacamole starts. By default this is false and the header extension will not be loaded. |
HTTP_AUTH_HEADER | Optional environment variable that, if set, configures the name of the HTTP header that will be used used to authenticate the user to Guacamole. If this is not specified the default value of REMOTE_USER will be used. |
If you have your own or third-party extensions for Guacamole which are not supported by the Guacamole Docker image, but are compatible with the version of Guacamole within the image, you can still use them by providing a custom base configuration using the GUACAMOLE_HOME environment variable:
| Variable | Description |
|---|---|
GUACAMOLE_HOME | The absolute path to the directory within the Docker container to use as a template for the image's automatically-generated |
You will still need to follow the steps required to create the contents of GUACAMOLE_HOME specific to your extension (placing the extension itself within GUACAMOLE_HOME/extensions/guacamole.properties, etc.), but the rest of Guacamole's configuration will be handled automatically, overlaid on top of a copy of the GUACAMOLE_HOME you provide.
Because the Docker image's GUACAMOLE_HOME environment variable must point to a directory within the container, you will need to expose your custom GUACAMOLE_HOME to the container using the -v option of docker run. The container directory chosen can then be referenced in the GUACAMOLE_HOME environment variable, and the image will handle the rest automatically:
Once the Guacamole image is running, Guacamole should be accessible at http://, where HOSTNAME:8080/guacamole/HOSTNAME is the hostname or address of the machine hosting Docker, and you should a login screen. If using MySQL or PostgreSQL, the database initialization scripts will have created a default administrative user called 'guacadmin' with the password 'guacadmin'. You should log in and change your password immediately. If using LDAP, you should be able to log in as any valid user within your LDAP directory.
If you cannot access Guacamole, or you do not see a login screen, check Docker's logs using the docker logs command to determine if something is wrong. Configuration parameters may have been given incorrectly, or the database may be improperly initialized:
| Prev | Up | Next |
| Chapter 2. Installing Guacamole natively | Home | Chapter 4. Proxying Guacamole |
The release page has pre-compiled binaries for Mac OS X, Windows, Linux and FreeBSD .The Linux binary is a static executable that can be run on any Linux distribution.
If you use macOS Homebrew, then you can install PostgREST from the official repo.
If you use FreeBSD, then you can install PostgREST from the official ports.
If you use Arch Linux, then you can install PostgREST from the official repo.
If you use Nix, then you can install PostgREST from nixpkgs.
If you use Windows, you can install PostgREST using Chocolatey or Scoop.
When a pre-built binary does not exist for your system you can build the project from source.
Running¶
If you downloaded PostgREST from the release page, first extract the compressed file to obtain the executable.
Now you can run postgrest with the --help flag to see usage instructions:
The PostgREST server reads a configuration file as its only argument:
Docker Postgres Install Extension Tool
For a complete reference of the configuration file, see Configuration.
Note
Docker Postgres Install Extension Chrome
If you see a dialog box like this on Windows, it may be that the pg_config program is not in your system path.
It usually lives in C:ProgramFilesPostgreSQL<version>bin. See this article about how to modify the system path.
To test that the system path is set correctly, run pg_config from the command line. You should see it output a list of paths.
To use PostgREST you will need an underlying database. We require PostgreSQL 9.4 or greater, but recommend at least 9.5 for row-level security features.You can use something like Amazon RDS but installing your own locally is cheaper and more convenient for development.
You can get the official PostgREST Docker image with:
The image consults an internal /etc/postgrest.conf file. To customize this file you can either mount a replacement configuration file into the container, or use environment variables. The environment variables will be interpolated into the default config file.
These variables match the options shown in our Configuration section, except they are capitalized, have a PGRST_ prefix, and use underscores. To get a list of the available environment variables, run this:
You can also specify a config file by mounting the file to the container:
There are two ways to run the PostgREST container: with an existing external database, or through docker-compose.
The first way to run PostgREST in Docker is to connect it to an existing native database on the host.
Docker Postgres Install Extension Tutorial
The database connection string above is just an example. Adjust the role and password as necessary. You may need to edit PostgreSQL’s pg_hba.conf to grant the user local login access.
Note
Docker on Mac does not support the --net=host flag. Instead you’ll need to create an IP address alias to the host. Requests for the IP address from inside the container are unable to resolve and fall back to resolution by the host.
You should then use 10.0.0.10 as the host in your database connection string. Also remember to include the IP address in the listen_address within postgresql.conf. For instance:
Docker Compose Postgres Install Extension
You might also need to add a new IPv4 local connection within pg_hba.conf. For instance:
To avoid having to install the database at all, you can run both it and the server in containers and link them together with docker-compose. Use this configuration:
Go into the directory where you saved this file and run docker-composeup. You will see the logs of both the database and PostgREST, and be able to access the latter on port 3000.
If you want to have a visual overview of your API in your browser you can add swagger-ui to your docker-compose.yml:
Docker Postgres Install Extensions
With this you can see the swagger-ui in your browser on port 8080.
Assuming your making modifications locally and then pushing to GitHub, it’s easy to deploy to Heroku.
- Create a new app on Heroku
- In Settings add the following buildpack
https://github.com/PostgREST/postgrest-heroku - Add the require Config Vars in Heroku (see https://github.com/PostgREST/postgrest/blob/master/app.json#L7-L57 for more details)
- Modify your postgrest.conf file as required to match your Config Vars in Heroku
- Create your
Procfileand add./env-to-config./postgrestpostgrest.conf - Push your changes to GitHub
- Set Heroku to automatically deploy from Master and then manually deploy the branch for the first build
